Intro
There are numerous reasons why almost all businesses within all sectors, and an increasing number of public and governmental institutions, move their data storage and processing onto cloud computing platforms. Better services, scalability, cost efficiency and accessibility are key elements. It is also increasingly clear that the security is easier to maintain and is significantly improved in well-designed cloud environments, where security protocols and encryption are built into the entire infrastructure by default, compared to most on-premises environments. Continuous software updates and market-leading hardware combined with organisational measures and physical security according to international standards makes it nearly impossible to compete with the leading cloud providers such as Amazon Web Services and Microsoft Azure. But cloud computing undeniably has some inherent issues that were identified in the Schrems II judgement (1) and pointed out in a detailed manner in the new EDPB-guidelines (2).
The Achilles’ heel of cloud computing
The issue at stake in the Schrems II judgement, by the Court of Justice of the European Union (CJEU), was the US ownership of the cloud providers (AWS, Microsoft Azure and Google Cloud), and the unsustainable legal jeopardy the companies may find themselves in, by being subjected to European privacy laws that conflict with US security and surveillance laws. Even though data is stored and processed in data centres physically located in Europe, the US ownership itself represents a risk for potential transfer of data to the US upon a binding US court order for data disclosure. This risk may be small - and it appears to be more of a theoretical concern for the vast majority of data controllers and processors than relevant in the practical world (3, 4). But the issue is more profound than the focus in the Schrems II ruling itself, as it pinpoints the trust all customers of cloud providers must put in their vendor, namely that they do not disclose or inappropriately access any data. This element of trust has always been the Achilles’ heel of public cloud computing and is particularly important in relation to the processing of sensitive data.
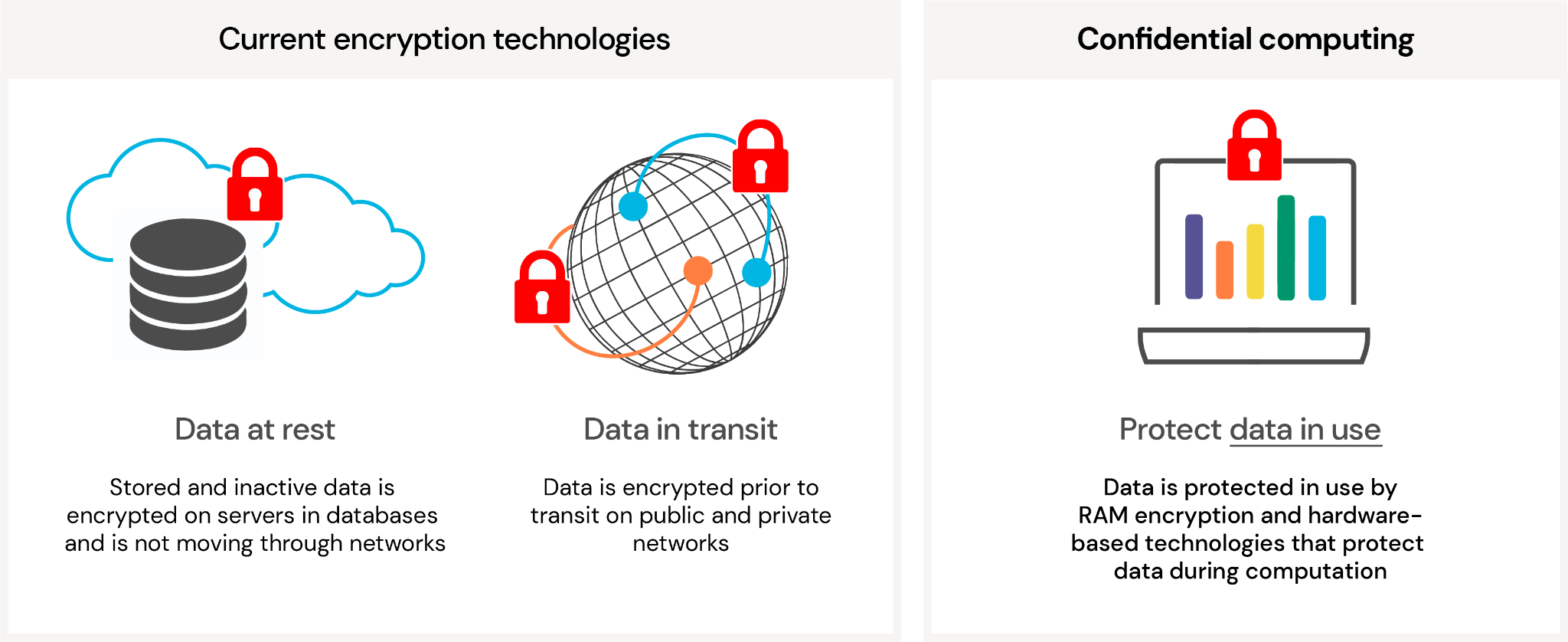
User authentication and encryption are two of the key tools developers use for securing data in the cloud. Data exists in three states: In transit, at rest (stored) and in use. However, encryption has only been technically possible on a large scale for data in transit and when stored, and not when the data are used (during data processing in computer RAM). Encryption makes the data useless and is fundamental to preserve data privacy and security. To strengthen the security and “compensate” for the lack of encryption of the data throughout the entire data flow, contractual and organisational measures are a part of the equation. For processing of sensitive data, this may represent an unacceptable reliance on non-technical measures. As long as there is a theoretical possibility that the cloud provider may access and read your or my data (and potentially transfer them to US authorities), there will be some level of uncertainty. Furthermore, this begs for the following question: Since it may not be possible to completely protect the data from the cloud operators, who else may access and read our data (if they successfully breach the other defence barriers that have been put in place)?
Confidential computing
Protecting the data in use is critical to offer complete security across the data lifecycle, and this is where confidential computing enters the scene - technologies that “isolate” sensitive data during processing from the cloud provider and all unauthorized personnel (5). The aim is to significantly improve the security and privacy of cloud computing and establish a hardware-based root of trust of the data processing. By making the data in use inaccessible or completely uninterpretable by encryption, the reliance on organisational and contractual commitments is less important. The concept of “root of trust” is the key, and we will return to that later. There have been several definitions of the term “Confidential computing” from when it was introduced, but regardless of the wording, the essence is that “Confidential Computing protects data in use by performing computation in a hardware-based Trusted Execution Environment (TEE). These secure and isolated environments prevent unauthorized access or modification of applications and data while they are in use, thereby increasing the security level of organisations that manage sensitive and regulated data” (6). The TEE, also called an enclave, executes the code and isolates and protects the code and data from the host system (plus the host system’s owners, e.g. the cloud provider), and may also provide code integrity and attestation that can be used for compliance and regulatory purposes. In the TEE, the data is secure in the memory, when traveling to and from the host CPU, and finally, during execution on the host CPU.
The driving force behind the technologies that made confidential computing a reality has been the need to completely prevent the cloud operators from being able to access interpretable data (data in plain text). To prevent unauthorized third-party access to data in use in the public cloud has been one of the major barriers to cloud adoption for highly regulated organisations where data privacy is critical. It is obvious that this technology dramatically improves privacy and security overall, but it is interesting that the need for complete technical “isolation” of the customer's data from the cloud operators has been a primary driver. The concept of confidential computing was introduced in 2018, and the major cloud providers, hardware manufacturers and software companies have worked diligently on this issue (7, 8, 9). The Schrems II judgement appears to have arrived in a timely manner to speed up the technical development and the full-scale implementation. Now, it is available for all to use (10). This means that the entire flow of data in a well-designed cloud environment is protected; from login with authentication mechanisms such as two-factor authentication, to encryption of data in transit, encryption of stored data, and now finally and critically, protection of data in use by memory encryption or other hardware-based technologies (11, 12, 13). Needless to say, this has until now been the missing link in data security in cloud computing, and it makes it possible for European businesses, public organisations, governmental institutions and others that are entrusted with our most sensitive data to continue their transition into the cloud. From a compliance point of view, it radically reduces the complexity as technical measures alone are sufficient to protect the data (2) and it also reduces the impact of the legal uncertainty related to the process of reaching a new Privacy Shield agreement between the EU and US (14).
Confidential computing is now listed as state-of-the-art in the newly released version of "Guideline State of the art - Technical and Organisational measures" by European Union Agency for Cybersecurity (ENISA) and IT Security Association Germany (TeleTrusT) (15). This corresponds to the protection requirement when cloud services are used for critical infrastructures or for sensitive data processing processes, e.g. in medicine, industry or in regulated areas (16).
Even though confidential computing solves an important compliance issue regarding the use of the major cloud providers for data processing within Europe and for transfer of data to third countries approved by the EU (17), the problem of transferring personal information to the US remains. However, this is mainly related to GDPR in general and not specifically the mechanism of the transfer, which was the focus of the Schrems II judgement. For our mutual benefit, we need to re-establish the transatlantic trust to advance our historically close relationship, as transfer of personal data is both a crucial and unavoidable component in most transactions, collaborations and business activities (18).
Hardware-based root of trust
A hardware-based root of trust is the basis for confidential cloud computing. In a trust hierarchy, the hardware itself is the foundation that all the other layers of trust are laid upon, such as the BIOS (Basic Input/Output System), operating system, firewalls, security software, physical security, and ultimately organisational and contractual measures. If the data in use is protected by the hardware itself, which is designed in a manner that is inherently resistant to malware injection and tampering, the memory is encrypted, and the hardware cannot be accessed in any way by any ports or APIs by any unauthorized persons including the cloud operators, then we are able to reach our security objective which is to protect the data end-to-end: In transit, at rest and in use. This is now becoming the reality.
In conclusion, full-scale employment of the technologies underpinning confidential cloud computing makes it possible to process the most sensitive private information in the cloud, such as personally identifiable health information, in a secure manner and in compliance with the EU-GDPR and the EDPB guidelines. Ledidi is now taking the necessary measures to employ confidential computing on our workloads in line with our commitment to do our utmost to preserve the security, privacy, and integrity of all sensitive data we are entrusted to process on behalf of our users.
References
1) European Parliament. The CJEU judgment in the Schrems II case. https://www.europarl.europa.eu/RegData/etudes/ATAG/2020/652073/EPRS_ATA(2020)652073_EN.pdf
2) European Data Protection Board. Recommendations 01/2020 on measures that supplement transfer tools to ensure compliance with the EU level of protection of personal data. https://edpb.europa.eu/our-work-tools/our-documents/recommendations/recommendations-012020-measures-supplement-transfer_en
3) Amazon. Law Enforcement Information Requests. https://www.amazon.com/gp/help/customer/display.html?nodeId=GYSDRGWQ2C2CRYEF
4) U.S. Department of Commerce. Information on U.S. Privacy Safeguards Relevant to SCCs and Other EU Legal Bases for EU-U.S. Data Transfers after Schrems II. https://www.commerce.gov/sites/default/files/2020-09/SCCsWhitePaperFORMATTEDFINAL508COMPLIANT.PDF
5) Ramon Krikken, Bart Willemsen. Top Strategic Technology Trends for 2021: Privacy-Enhancing Computation. Gartner. https://www.gartner.com/document/code/740641???ref=ihc-interactivesection-hc
6) The Confidential Computing Consortium. Confidential Computing: Hardware-Based Trusted Execution for Applications and Data. 2021. https://confidentialcomputing.io/wp-content/uploads/sites/85/2021/03/confidentialcomputing_outreach_whitepaper-8-5x11-1.pdf
7) The Confidential Computing Consortium. What is the Confidential Computing Consortium? https://confidentialcomputing.io/
8) Amazon. AWS Nitro System. https://aws.amazon.com/ec2/nitro/
9) Xilinx. It’s No Secret: Why Xilinx Joined the Confidential Computing Consortium. 2020. https://zephyrnet.com/its-no-secret-why-xilinx-joined-the-confidential-computing-consortium/
10) David Brown. Confidential computing: an AWS perspective. AWS Security Blog. https://aws.amazon.com/blogs/security/confidential-computing-an-aws-perspective/
11) Amazon. AWS Graviton Processor. https://aws.amazon.com/ec2/graviton/
12) Danilo Poccia. New – Amazon EC2 M6i Instances Powered by the Latest-Generation Intel Xeon Scalable Processors. AWS News Blog. https://aws.amazon.com/blogs/aws/new-amazon-ec2-m6i-instances-powered-by-the-latest-generation-intel-xeon-scalable-processors/
13) Intel Xeon Scalable Platform Built for Most Sensitive Workloads. Intel Corporation. https://www.intc.com/news-events/press-releases/detail/1423/intel-xeon-scalable-platform-built-for-most-sensitive
14) Ryan Chiavetta. Hoff: EU, US 'not at the beginning' of Privacy Shield negotiations. IAPP. https://iapp.org/news/a/hoff-eu-us-not-at-the-beginning-of-privacy-shield-negotiations/
15) https://www.teletrust.de/filea...
16) https://www.enisa.europa.eu/ne...
17) The European Commission. Adequacy decisions. https://ec.europa.eu/info/law/law-topic/data-protection/international-dimension-data-protection/adequacy-decisions_en
18) Nigel Cory, Ellysse Dick. How to Build Back Better the Transatlantic Data Relationship. The Information Technology and Innovation Foundation. https://itif.org/publications/2021/03/25/how-build-back-better-transatlantic-data-relationship